Where we are Link to heading
We already have some quality materials - like the Microsoft Cybersecurity Reference Architecture - about the security best practices of the Azure Cloud including possibly everything related to Cybersecurity but I feel that something is missing and I’ll tell you why in a moment.
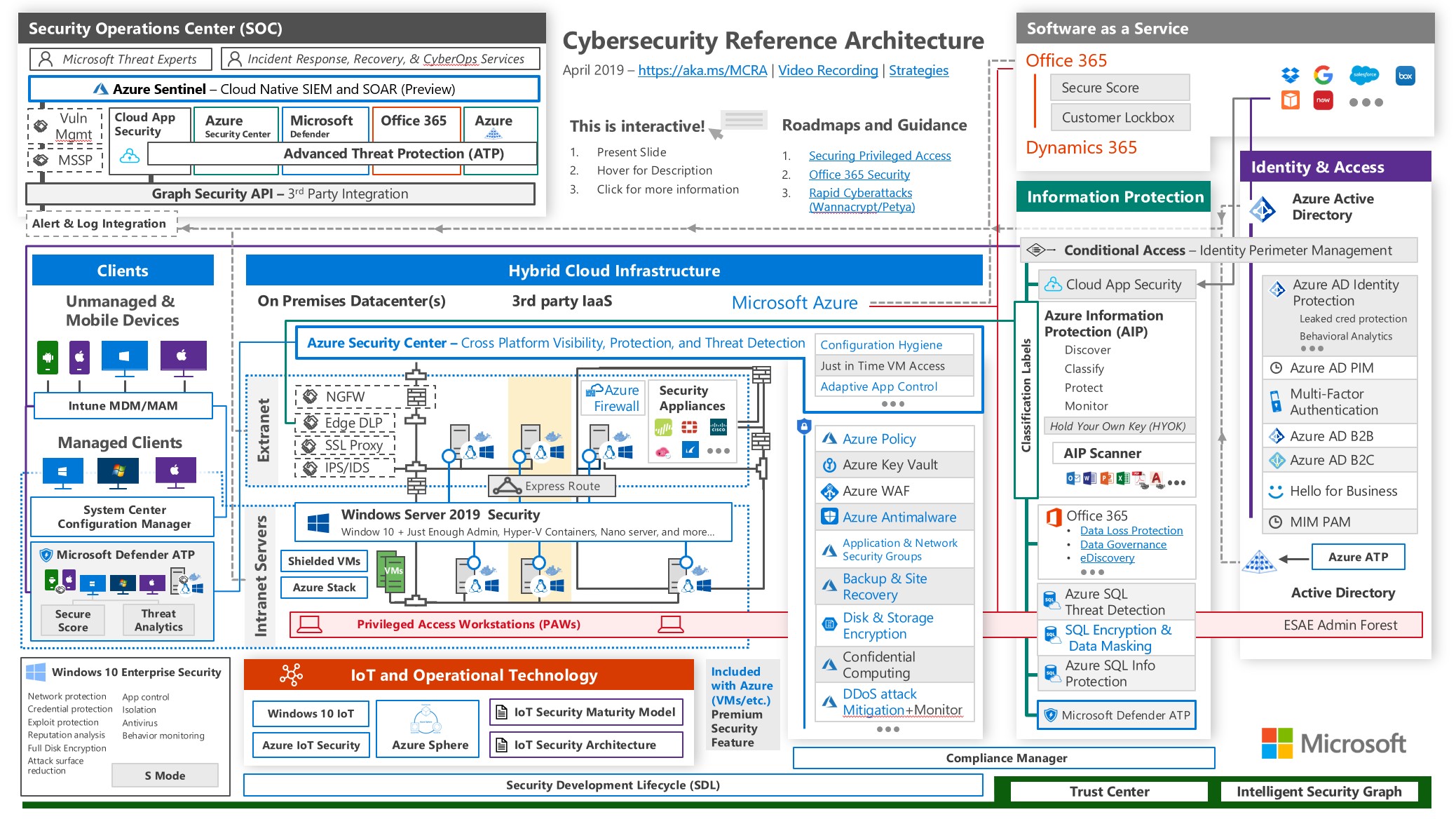 If you take a closer look at the reference material you’ll see a red bar titled:
If you take a closer look at the reference material you’ll see a red bar titled: Privileged Admin Workstations (PAWs) and in the right side of that bar you’ll see ESAE Admin Forest which is described here ESAE Administrative Forest Design Approach
ESAE stands for Enhanced Security Administrative Environment
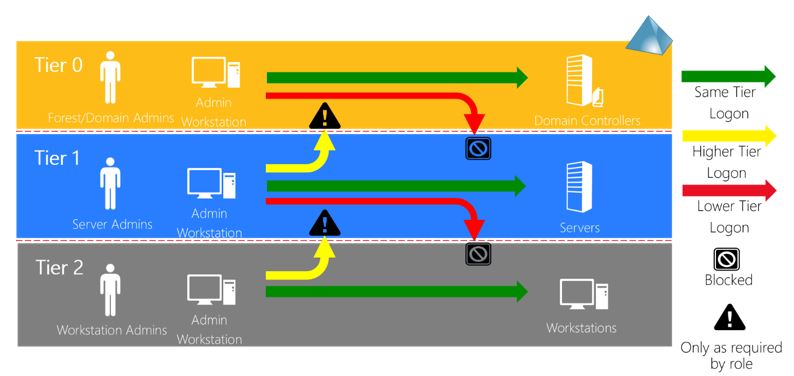
Stop for a moment and think about why would we need a dedicated admin forest to manage the PAW boxes? The answer is in the Active Directory administrative tier model which is described at the top of the article.
The challenge Link to heading
The challenge we face here is that someone has to manage the PAW machines which are used to conduct highly privileged activities but the group responsible for the PAWs should not be the same group which manages the productivity devices of the rest of the organization. But as of today (5/26/2019) we cannot do that using Azure AD and Intune. The Device Administrator role has rights to manage all Intune managed devices, which does not meet the requirements of the previously mentioned tier model.
Within larger or more security focused companies there is a clear segregation of duties and segregation of infrastructure elements as well. Not because we don’t trust our admins but because they are the targets of attackers. In an unfortunate event where a machine or an account used by an admin gets compromised the attacker will have much better odds to achieve its goals.
The solution Link to heading
Following the Reference Architecture, we must segregate the PAW boxes from the rest of the organization and the only option to do that is to create the cloud version of the ESAE Admin Forest.
I like to call it
Red Cloud
In practice Link to heading
We’ve to create a new Azure AD environment, I suggest purchasing Microsoft 365 E5 licenses for this environment and something lightweight like the Surface Pro 6 to be used as the PAWs. Using M365 E5, the PAW machines can run Windows 10 Enterprise, be managed by Intune and be protected by Microsoft Defender ATP and everything else which is suggested or will be suggested by these pages Defender Secure Score and Level 1 enterprise administrator workstation security configuration (work in progress).
We’ve to invite these Red Cloud accounts into our Production Tenant as B2B guest accounts and convert them into members using the AzureAD PowerShell module and the following cmdlet:
Set-AzureADUser -UserType Member.We’ll have to grant them licenses in the Production Tenant. I suggest the followings: AAD Premium P1 & P2, Azure Advanced Threat Protection, Azure Information Protection Premium P1 & P2, Microsoft Azure Multi-Factor Authentication, Microsoft Cloud App Security, Microsoft Intune, Windows 10 Enterprise, Windows Defender ATP.
Using Azure Active Directory Privileged Identity Management (PIM), we can grant the required roles for the Red Cloud accounts. These roles can be: Global Admin, Security Administrator, etc.
Limitations Link to heading
Not everything works together nicely with the Red Cloud approach, based on my experience the Azure AD Portal and the Azure ATP portal works just fine, but the Microsoft Cloud App Security and the Microsoft Defender ATP portal do not support the guest accounts, I hope this will change in the future.
Fortunately, these limitations do not affect our goal here :)
We wanted to have the ability to manage the PAWs from a different Tenant and not from the Production environment where the productivity devices are located, and we achieved this. We can logon to the PAW boxes and access the Production AAD using our Red Cloud IDs and leverage PIM to elevate our access level and manage the Tenant as we see fit.
In the other way around, the Device Administrators of the Production Tenant cannot control the PAW boxes and we’ll be protected in case an attacker manages to breach any of our device administrators of the Production Tenant.